Getting Started with Bloodhound
Install and ingest some sample data to begin the journey with AD auditing using Bloodhound.
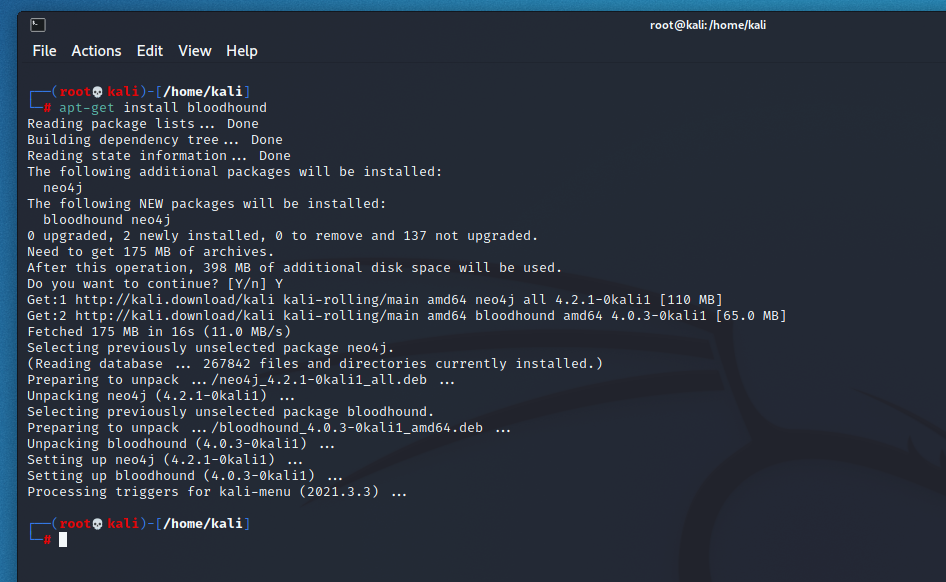
Install Bloodhound
Installing Bloodhound is a relatively simple task and we used the latest version of Kali (2021.3) for this.
apt-get install bloodhound
Start and Configure Neo4j
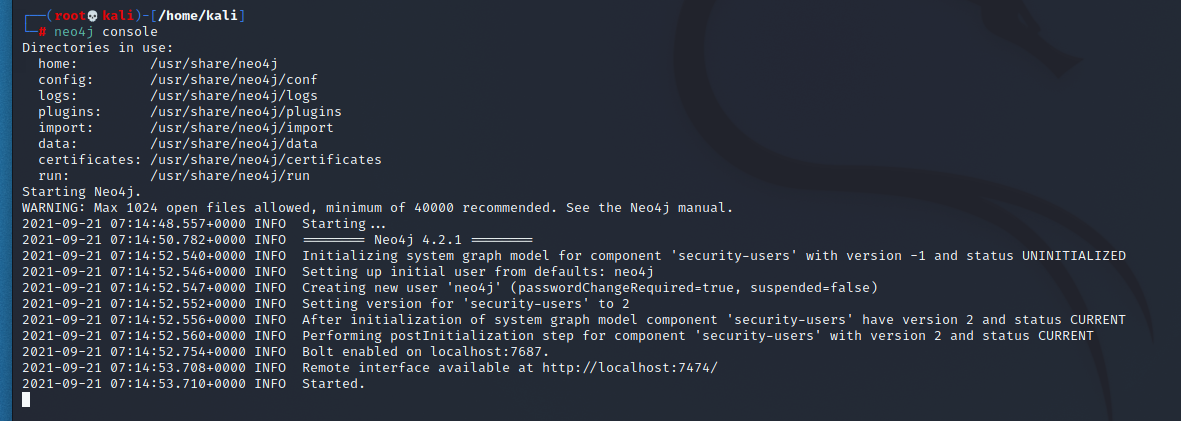
The backend of Bloodhound is powered by a graph database called Neo4j. We’ll need to start that and change the default password for the Bloodhound front end to connect to.
neo4j console
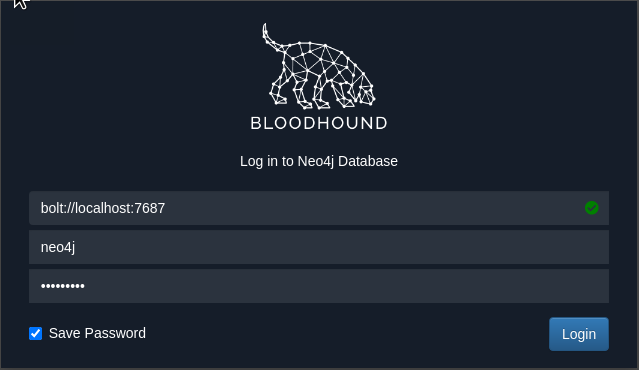
Open a web browser and navigate to the following URL to change the password.
http://localhost:7474/browser/
Now you can start Bloodhound and you'll be presented with the following screen. The green tick in the Bolt port section indicates the Neo4j instance is correctly running.
Once you've logged in you will see that Bloodhound is currently a blank slate.
Bloodhound Data
You can download a sample set of data from a test Domain Controller from the link below. All you require is the ZIP file, this has all of the JSON files extracted with SharpHound.
https://github.com/mike-nolan-councilman/Bloodhound_Data
The Active Directory data was populated using BadBlood which is available in the following repository. Please note that the data does not include any session information and so some of the session based queries will not return data.
https://github.com/davidprowe/BadBlood
Import Data and Perform Queries
Copy across the 20210920185958_BloodHound.zip ZIP file to your Kali VM. From there you can select the Upload Data button on the righthandside menu items and select the ZIP file. You will be presented with an summary screen and once complete this can be closed. Bloodhound will now be populated with the data and you can begin executing queries
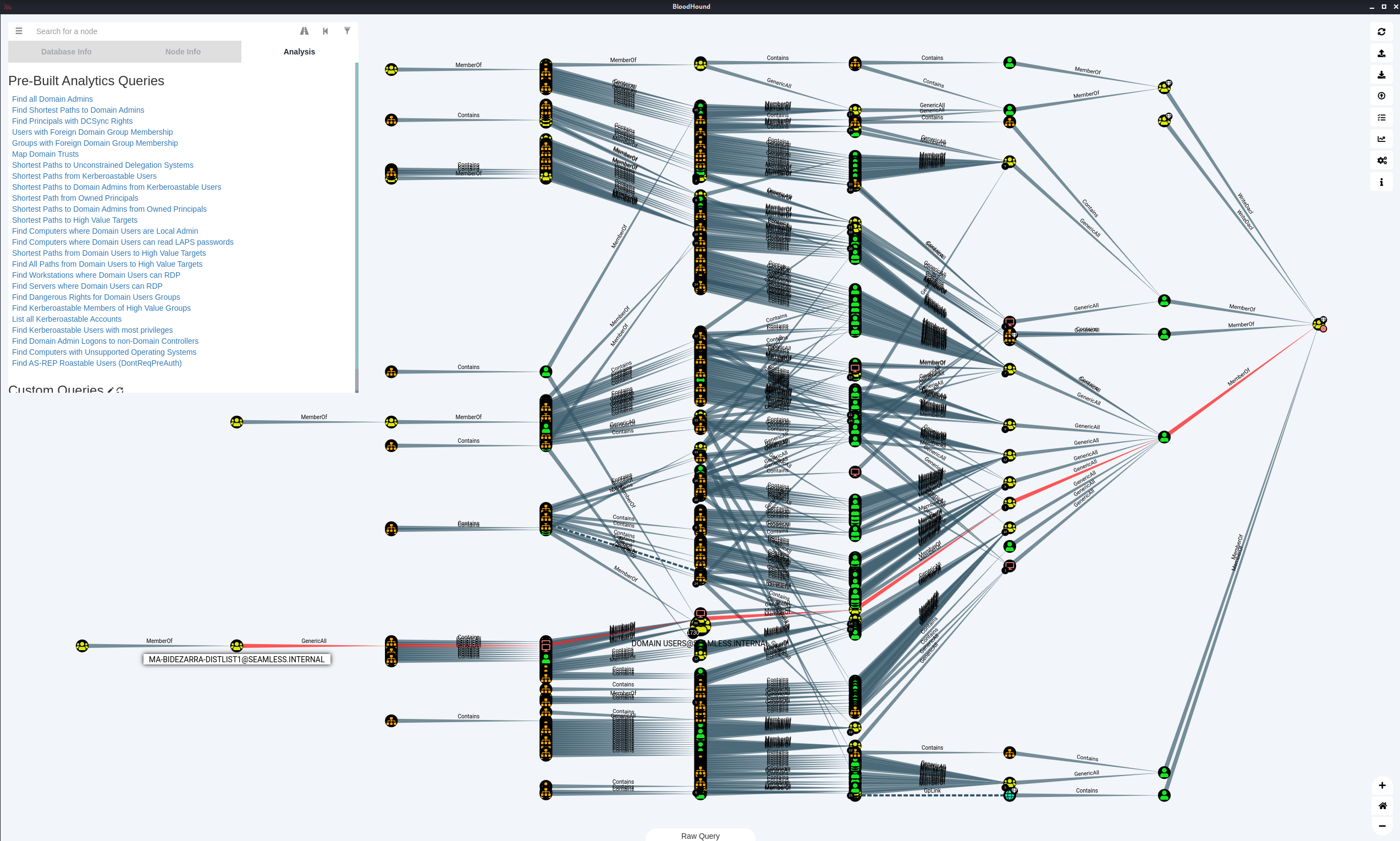
Shortest Paths to Domain Admin
Below shows the shortest path to Domain Admins for the data set. This is a good first query and from here you can further explore the data.
TargetedKerberoast
The below manual query can be used to assist in detecting account suspectable to TargetedKerberoast. This query will not return any results in the sample data set however the next query removes the exclusion for the Administrators group and when we run that we will discover that >2000 accounts are in the Administrators group, not great if it was real world.
MATCH p=(g:Group)-[r:GenericWrite]->(u:User) WHERE NOT (g.name =~ '(?i)domain admins@.*' OR g.name =~ "(?i)enterprise admins@.*"OR g.name =~ "(?i)administrators@.*"OR g.name =~ "(?i)organization management@.*"OR g.name =~ "(?i)exchange servers@.*") RETURN p
MATCH p=(g:Group)-[r:GenericWrite]->(u:User) WHERE NOT (g.name =~ '(?i)domain admins@.*' OR g.name =~ "(?i)enterprise admins@.*") RETURN p
Cypher Queries
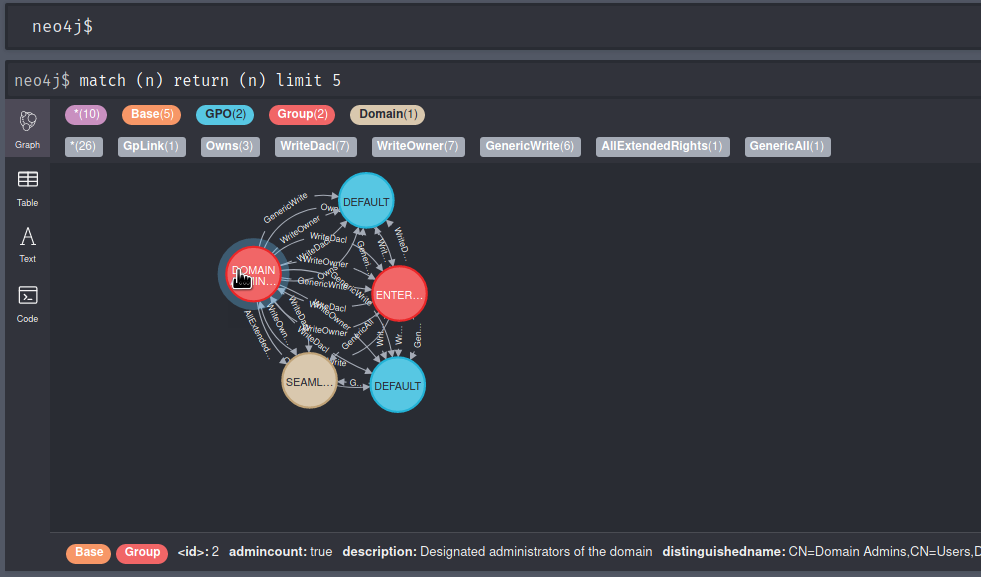
You can also see the graph database in action once logged in via a web browser. The below cypher query will return 5 results with their relationships and you can see the amount of data that is actually being written and processed in the background.
match (n) return (n) limit 5